MODIFIED ON: November 25, 2022 / ALIGNMINDS TECHNOLOGIES / 0 COMMENTS

With the emergence of advanced technologies, there is an increase in information sharing through social networking sites and using the web for doing business. As a reason, websites are being hacked more than often. Majority of website attacks happens due to imperfection in coding and failure to sanitize input to and output from the web application. Here are some of the software security issues that we face today.
1. SQL injection
An SQL injection is one of the mechanisms used by hackers or attackers to steal data from organizations. SQL injection as the name suggests it is the process of injecting malicious SQL statement into the application where the hacker or attacker has the access to back end database.
It helps the attacker or hacker to create, update, read, alter or delete the data stored in the back-end database. Once the attacker understands the system is vulnerable to SQL injection the hacker or attacker can inject SQL commanhds through an input field, which helps an attacker to take control of the database where he can execute various Queries.

SQL injection can be prevented by providing validation for the fields where the user input is authenticated for specific length type and business requirements.
Also, remove all the stored procedures that are not in use to improve your software security.
2. Cross-Site Scripting (CSS or XSS)
XSS allows the attacker to inject client-side script into Web pages viewed by other users. These may be used by attackers to bypass access controls. By using cross-site scripting the attacker or hacker can inject malicious Javascript, VBScript, Flash, ActiveX into a dynamic web page to gather all the data executing these scripts. Mainly web server applications that generate the page dynamically are vulnerable to Cross-site Scripting if there is no proper validation for user input and to ensure that pages generated are encoded properly.
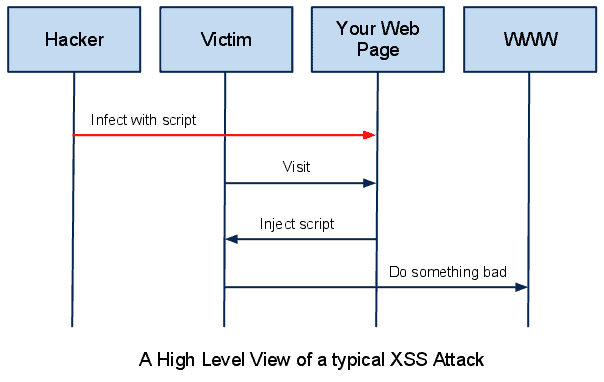
Two types of Cross-Site Scripting are Persistent and Non-Persistent.
Persistent
A persistent type of CSS is done when the attacker enters the malicious data to the web application and the entered data is permanently stored in the database. In this case, each and every person visiting the page will be a victim of Cross-site scripting. This affects every user of the website as it is stored in the database permanently.
Non Persistent
The malicious code injected by the attacker is executed on the users’ browser and the code is not stored anywhere it is executed along with the response from the server.
3. Cross-Site Request Forgery
A malicious website will send a request to a web application where the user has already entered the credentials through a different website. Like this a hacker can access all the functionalities in a target web application via the victims already authenticated browser.
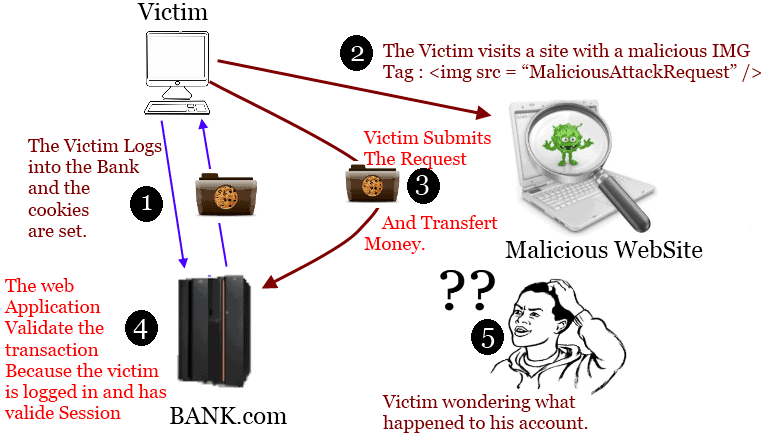
In these cases, the malicious request is sent from the attackers’ website to another site the user has validated against.
The malicious requests are sent to the target site through the victim’s browser, which is authenticated against the target site.
Cross-Site Request Forgery can be prevented by inserting unpredictable challenge tokens to each request and associating with the user’s session. Each token created will be unique for each session. By including these tokens, the programmers can be sure that the request is valid and not coming from other sources.
4. URL redirection
URL redirection happens when a user clicks on a link on the vulnerable website takes him to an untrusted website. This way an attacker can redirect web user to other websites which are used for phishing and similar attacks. These URL redirections can pass the applications access control check and make the attacker use the privileged functions that they would normally not able to access.

These kinds of URL redirection can be prevented by
- Do not use users’ input for URL
- If dynamic URLs are used Make a list of the valid URLs and never accepts invalid URLs
- Always make sure that the accepted URLs are located on the accepted domains.
- Make all the redirects to first go through a page notifying users that they are going off your site and have a confirmation link to click.
5. OS Command Injection
OS command injection is a technique used to inject the OS command through the web interface to execute it on the Server. Any web interface that is not properly coded will be subject to this attack. With these, the user can upload malicious programs or even obtain passwords if the attacker is successful in executing OS commands. These threats occur because the application fails to validate and sanitize the parameters invoking shell functions such as system() or exec() to execute system commands.

Types of command Injection
- Direct command injection
- Indirect command injection.
Direct Command Injection
In this case, the attacker understands the application invokes a system command as an argument to the command. Then passes the malicious command as a part of the expected arguments.
Indirect Command Injection
In this case, the additional commands are indirectly supplied to the vulnerable application through a file or environment variable. Once the attacker deducts that the application invokes a system command from an external source, then he modifies the contents from the external source to add a malicious command.
The best way to prevent OS Command injection is to sanitize the URL and form data for invalid characters. Also, a list of allowable characters should be created to validate user input. Characters that are misused and unwanted threats should be eliminated by this list.
Computer security is a vast topic that is becoming more important as all the transactions taking place are interconnected. If given proper attention to the coding standards and necessary validation for the field, we can have control over the main security threats happening.
Leave a reply
Your email address will not be published.
-
Recent Posts
- The Role of AI in Business Growth: Top Trends for 2025 and Beyond
- The Evolution of Voice Search in AI: What’s Next for 2025?
- How to Hire an AI Developer: A Complete Guide 2025
- Top 10 Android App Development Trends in 2025
- Top Trends in Product Modernization for 2025 and Beyond
-
Categories
- MVP Development (5)
- AlignMinds (56)
- Operating Systems (1)
- Android POS (3)
- Application Hosting (1)
- Artificial Intelligence (49)
- Big Data (2)
- Blockchain (1)
- Cloud Application Development (8)
- Software Development (39)
- Software Testing (9)
- Strategy & User Experience Design (4)
- Web Application Development (28)
- Cyber Security (6)
- Outsourcing (7)
- Programming Languages (3)
- DevOps (5)
- Software Designing (6)
- How to Code (4)
- Internet of Things (1)
- Machine Learning (2)
- Mobile App Marketing (5)
- Mobile Application Development (25)
- Mobile Applications (11)







