MODIFIED ON: November 29, 2022 / ALIGNMINDS TECHNOLOGIES / 0 COMMENTS

Securing data always remains a challenge while we are witnessing the growth of technology at an amazing pace. The more secured your website, the more the chances of users accessing your website.
Whether it is an e-commerce website, social media websites or any other company website, every website existing online is prone to one or the other form of security threat. It is very important to be aware of the web application security threats and be prepared for handling it.
Organizations now use advanced technologies and heavy security testing to keep their website safe and protect customer privacy. Security testing is not just restricted to the testing team, the development team also plays an important role in ensuring security constraints.
What’s the risk?
Hackers are increasing day by day who are in continuous search of the vulnerable website. It’s essential for an individual or an organization to take steps for protection of their data by improving the web application security. Although various tools and technologies are available to handle security threats, protecting your website is possible only by continued effort.
Hacked website is a terrible thing that causes a lot of distress to both the owner and the customers. A website that is a victim of abuse will poorly reflect on your business and brand.
Enough proactive measures must be taken to ensure all preventive steps are taken for better web application security in the long run.
Sources of web application security risks
The security threat to websites web apps and mobile apps come in many forms today. While online threats are continuously evolving, following are very popular among hackers:
Malware
Malware is nothing but short computer programs that attempt to get access to a computer without user consent. It can be virus, worm or Trojan.
Virus
Virus is a program written to damage or delete your files/contents from your computer.
Worms
Worms do not cause any harm to your data but replicate it again and again. Due to its replication nature, it takes lots of memory space degrading computer performance and consuming more network bandwidth.
Trojan
A Trojan horse is a destructive program (not a virus) that looks like a genuine application. Trojan horses do not replicate, but it enters your computer, can give access to your confidential information to unwanted users.
Spoofing
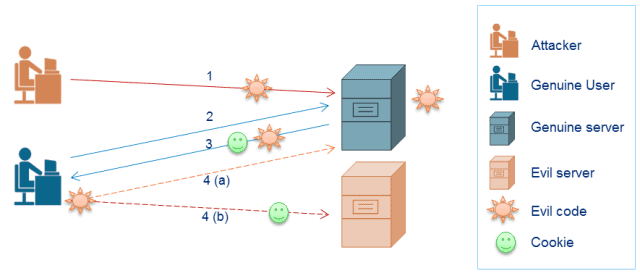
Computer or a user pretends to be another, usually, one who has higher privileges to attack system to damage data or to deny access. Many of the TCP/IP protocols do not provide a mechanism to authenticate the source or destination of a message. When extra precautions are not taken by applications to verify the identity of sending or receiving host, it becomes vulnerable to spoofing attacks. Firewalls can help prevent spoofing attacks.
Spamming
Electronic spamming is sending of messages repeatedly. There are many forms of Spamming like mobile phone-messaging spam, internet forum spam, junk fax transmissions, social spam, search engine spam etc. E-mail is the most widely recognized Spam.
Phishing
Hacker sends emails that look legitimate to the recipient asking for confidential information. Recipient falls into such tricks and provides the login information or other important banking details thus; hacker gets access to their confidential information.
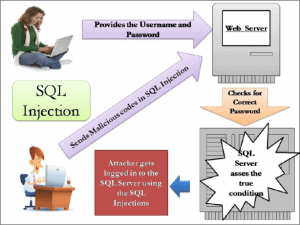
SQL Injection
SQL Injection is a Code Injection technique in which malicious SQL code is inserted into an entry field for execution. Top websites are vulnerable to Injection flaws especially, SQL Injection Flaws. By employing injections, a hacker can have your code run unintended commands or accessing unauthorized data.
How to ensure web application security?
SQL Injection
Here, the hacker makes use of web form field or URL parameter to manipulate data or to get sensitive data. For example, consider the following query to get login credentials:
ELECT * FROM Users WHERE user_id = ‘my’ and password=’test’;
Now, the hacker enters ‘OR 1 = 1; /* in Email id text field and */– in the password, the query on execution would look like:
SELECT * FROM Users WHERE user_id =’ ‘OR 1 = 1; /* and password=*/–
This will display all users in Users Table.
There are several automated scanning and detection tools available in the market to handle SQL Injection, however, the best way to avoid such attack is proper code review as complete coverage involves manual code review and manual testing along with usage of detection tools.
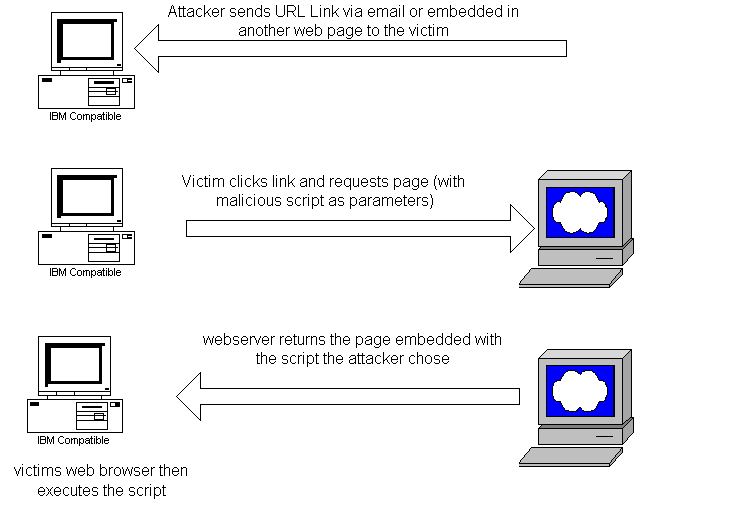
Cross Scripting
Cross Scripting (XSS or CSS) is one of the most common application layers hacking technique. Here, hacker attempts to insert JavaScript, VBScript, ActiveX, HTML etc code into the dynamic pages in an attempt to run malicious code.
The use of XSS might compromise private information, manipulate or steal cookies, execute malicious code to generate undesirable results, create request taking others’ identity. This is the most prevalent form of security attacks.
One way of protecting from XSS attack is to have all the code pass through some kind of filter that will omit keywords like <script> tags, JavaScript commands, CSS tags and other notorious HTML Markup (the ones that contain event handlers).
There are many libraries available to implement a filter mechanism, which one you choose will depend on your back-end technology. Ensure you always use updated filters for better security as XSS techniques keep changing and new ones keep emerging all the time.
Error Messages
Be careful about the error messages that get displayed when a user enters incorrect data. Always give generic messages. For example, when a user fails to enter the correct username/password, give a message like “Invalid username/password”. Giving exact information about what went wrong can give the hacker the clue that he has reached halfway correctly and need to focus only on the rest of the part.
Server/Browser side validation
Validation must be used at both browser and server end for better security. Simple failures like invalid phone format, numbers only, blank field etc. can be found by form validation itself; however, using stronger server-side validation can help prevent malicious code that can bring undesirable results in your website.
Password
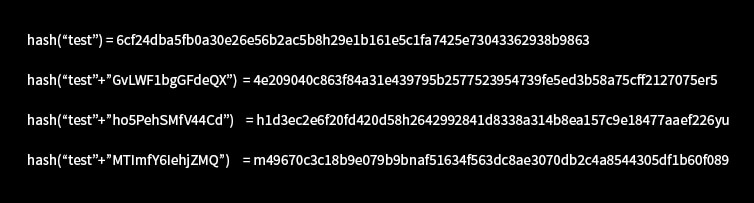
Always practice for using stronger passwords. Your password must be a combination of special characters, numbers and upper-case letters. Passwords must be hashed while storing in database.
In case your data get stolen, damage can be minimized if the password is encrypted as decrypting them would not be possible. Plain hashing is not enough for the security of passwords. You can make encryption more secured by adding salt to your password.
Salt is a randomly generated string inserted before or at the end of the password to generate randomized hashes. As shown in below example, it makes a password hash into a completely different string every time. Salt is stored in user account database along with hash, or as part of the hash string itself. Salt must not be re-used; new random salt must be generated every time the user creates a new account or change password.
File Uploads
In today’s modern web applications, it has become necessary to provide an option for file uploading. Various social networking applications like Facebook, Twitter etc, blogs, forums, and other websites provide the option to upload files, pictures, avatar, videos and several other kinds of files. The more this feature is available on the website, the more the website is prone to malicious attacks.
Sometimes an uploaded file may contain a malicious script that can just open up the entire site. Below are mentioned some best practices if implemented while uploading a file can help you have secure file uploads:
- Define a .htaccess (Hypertext Access) file – A configuration file used by Apache-based web servers that has the ability to password protect folders, deny access to unwanted users, redirect users to another page, change the way files with certain extensions are utilized etc.
- Do not place .htaccess file in the folder where your uploaded images will be preserved. Save it in the parent folder.
- Provide a list of acceptable extensions for a website in the .htaccess file with proper deny/allow permissions. That way only allowed files can be uploaded by any user and can also limit access to each file type.
- Always store files in a different folder outside of the webroot.
- Avoid overwriting of files (to prevent .htaccess overwrite attack)
- Create a list of acceptable mime-types
- Generate a random file name and add the previously generated extension. Use a unique file name to uniquely identify each file name.
- Implement both client-side and server-side validation for extra security.
SSL
SSL (Secure Sockets Layer) is a protocol used to provide security to websites over the Internet. If the communication channel is not secured while transmitting confidential information between website and web server or database, a hacker can easily get access to user accounts and personal information. SSL helps overcome this security threat by establishing a secured connection between browser and web server.
SSL allows confidential information like SSN, Credit Card details, login information etc to be transmitted securely over the network. SSL certificates have a key pair – public and private key. These keys work together to establish an encrypted connection.
The certificate also contains the identity of the website owner. Once the webserver has SSL Certificate installed and the communication between client and server is secured, it gives a trusted environment to the visitor indicating that their connection is secured. Browser assures visitors that their connection is secured by displaying a lock icon or a green bar and URL starts with https:// than “http:”
Conclusion
Do everything you can to improve web application security. Stay up-to-date, limit access to resources, use strong passwords and password storing techniques, and constantly monitor your site. These are some simple steps that if carefully considered can protect your data and website from hackers.
Leave a reply
Your email address will not be published.
-
Recent Posts
- Chatbots vs. Conversational AI: Decoding the Mysteries Behind the Tech
- Leading the Pack: The Top Conversational AI Platforms Transforming Communication in 2024
- The Future of Work: Key Remote Staffing Trends Dominating 2024
- The Ultimate Guide to Choosing the Right Generative AI Company
- How to Cut Through the Hype: A Practical Guide to Generative AI for Businesses
-
Categories
- MVP Development (3)
- AlignMinds (55)
- Operating Systems (2)
- Android POS (3)
- Application Hosting (1)
- Artificial Intelligence (18)
- Big Data (2)
- Blockchain (1)
- Cloud Application Development (7)
- Software Development (30)
- Software Testing (9)
- Strategy & User Experience Design (4)
- Web Application Development (23)
- Cyber Security (6)
- Outsourcing (7)
- Programming Languages (3)
- DevOps (5)
- Software Designing (6)
- How to Code (4)
- Internet of Things (1)
- Machine Learning (2)
- Mobile App Marketing (4)
- Mobile Application Development (18)
- Mobile Applications (5)







